OTP security
Newcastle Permanent - Internet and mobile banking
Social engineering fraud remains a significant threat to online security, particularly in the context of financial transactions and sensitive data access. As part of a larger project around digital customer protection, there was an opportunity to review existing One Time Password (OTP) messaging with a view to uplift their security effectiveness.
My Role: UX research, UX design, UX copy
Team: UX designer, Business Analyst, Various business SMEs
Time: 2 weeks
Challenge:
Traditional OTP systems often lack sophistication in their content, and in Newcastle Permanent’s case OTP content was essentially generic, making users vulnerable to social engineering attacks. Fraudsters exploit this weakness by impersonating legitimate entities, manipulating users into revealing OTPs, and gaining unauthorized access to accounts. Thus, there was a need to redesign OTP content to enhance its effectiveness in preventing social engineering fraud activities around OTP messages.
Limitations: Existing OTP functionality was to remain in place.
Research
Message considerations
First I considered a number of factors around standard formats around OTP messages and considered current message contents such as standard OTP structure, character limits, and content inclusions and limitations. Considerations included;
Keep existing components of OTP code, warning, and contact info.
SMS Message body should ideally be less than 160 characters (1 text message) - The size of message can impact SMS delivery and cost.
Keep terminology of “One-time password” - customer familiarity.
Maximum transaction amounts of $3,500,000.00.
Contact number format (13 19 87 or 131987) - Can affect click to call linking in certain message applications.
Google SMS phishing/smishing study
I did some further research around security and SMS verification, and in particular found interesting research around phishing incidents.
A study to determine the most effective SMS verification message against phishing was conducted by NYU in 2015.
The following proposed SMS message reduced phishing incidents from 60% to 8% when followed by an attack SMS message - "Please ignore this message if you did not request a code. Your Google verification code is 312985"
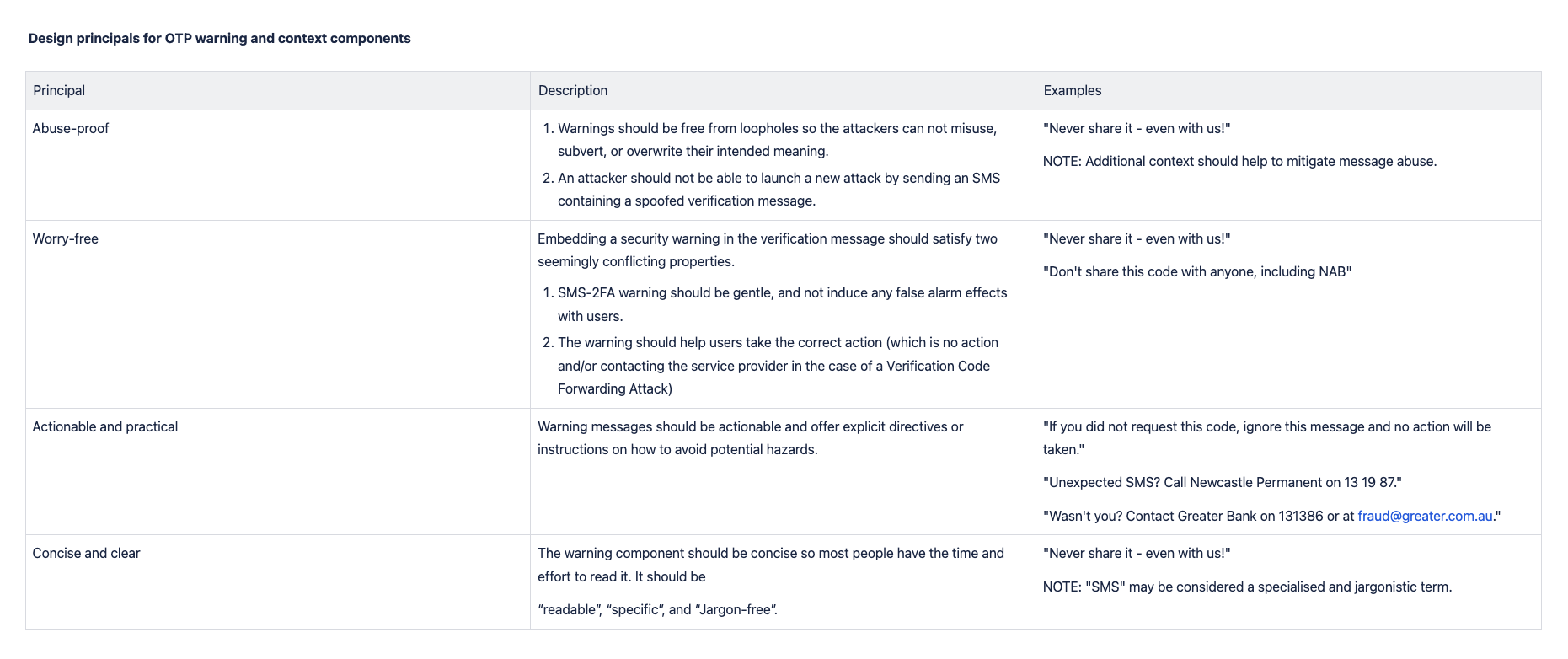
The message employed the design principles mentioned below, with a focus on conveying a warning to the user to take no action in the event of receiving an attack SMS message.
Interestingly the format of the message placed the warning at the beginning of the message to ensure its visibility.
For further information see Mind your SMSes: Mitigating social engineering in second factor authentication
Design principals for OTP warning and context components
Design Process
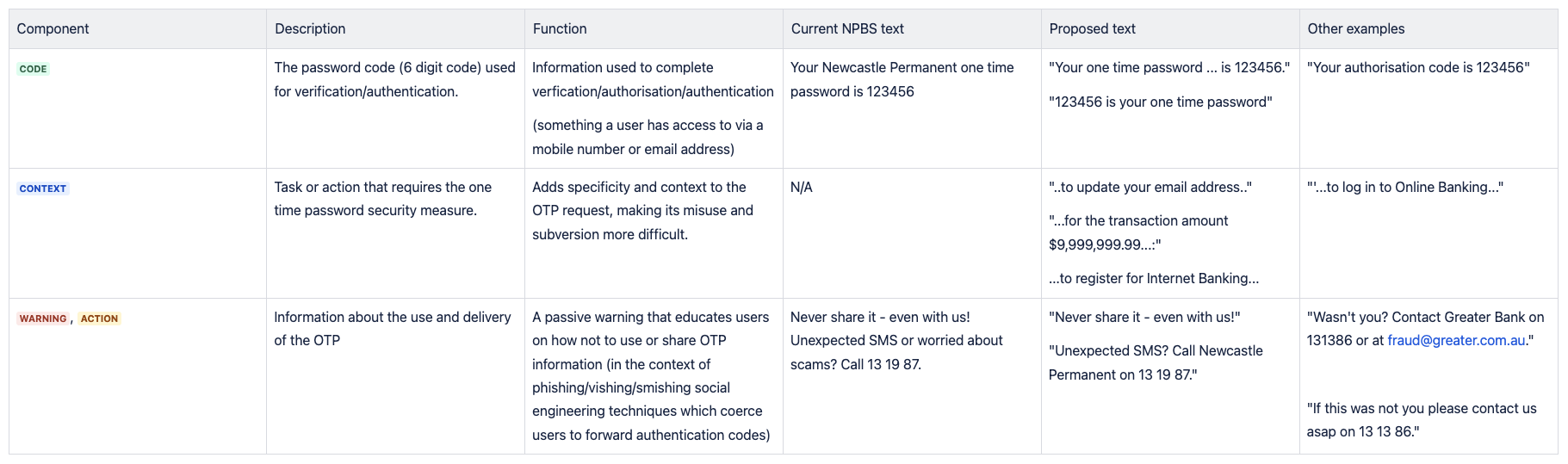
OTP message components
For the design process, I broke down OTP messages into discreet functional components of Code, Context, Warning and Action.
OTP component order
Next I explored different arrangements of components within the OTP message, with a focus on component importance and hierarchy. Each version was tested with staff and SMEs.
OTP component arrangements
Final messages and templates
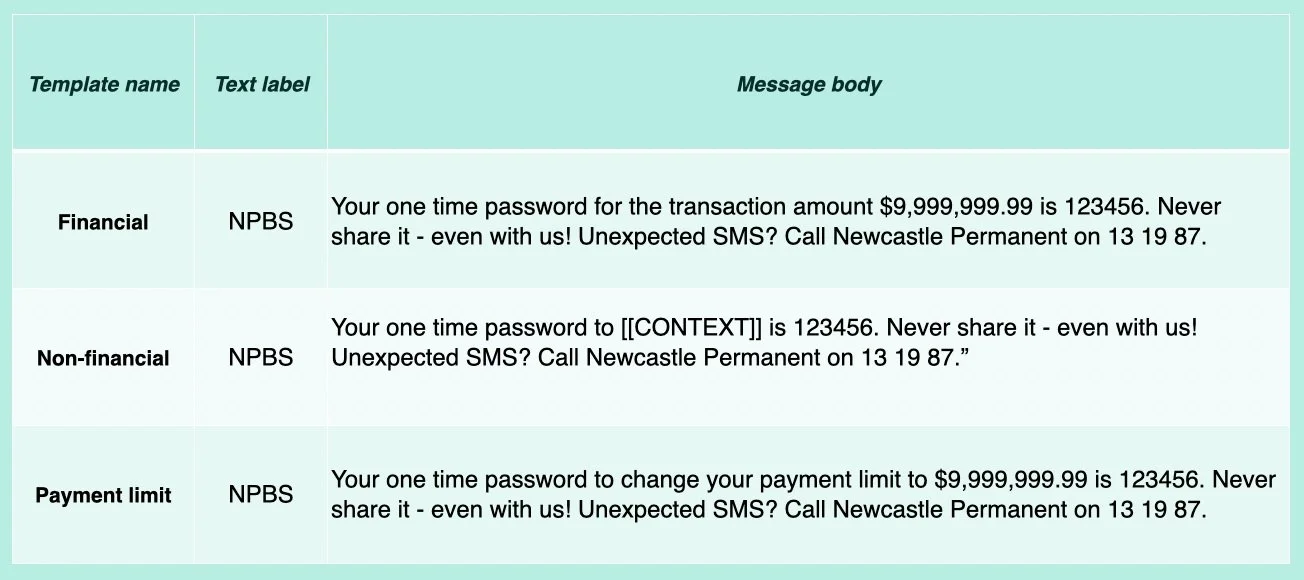
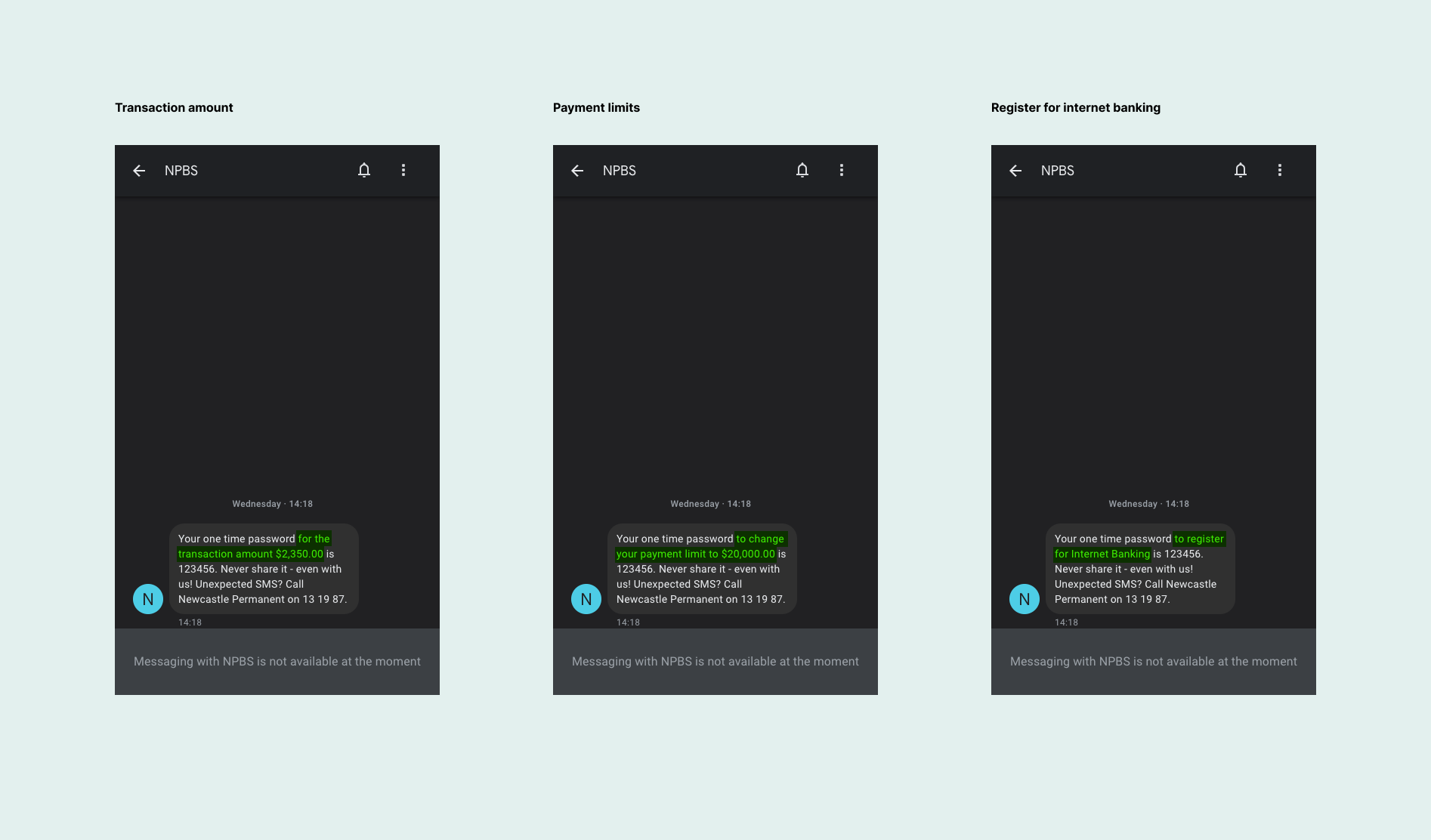
Messages were broken down into 3 types of Financial, Non-financial and Payment limit. Contextual information was separated to allow different types of content to be used for different OTP authentication scenarios.
Proposed SMS OTP message types
Solution
Final version
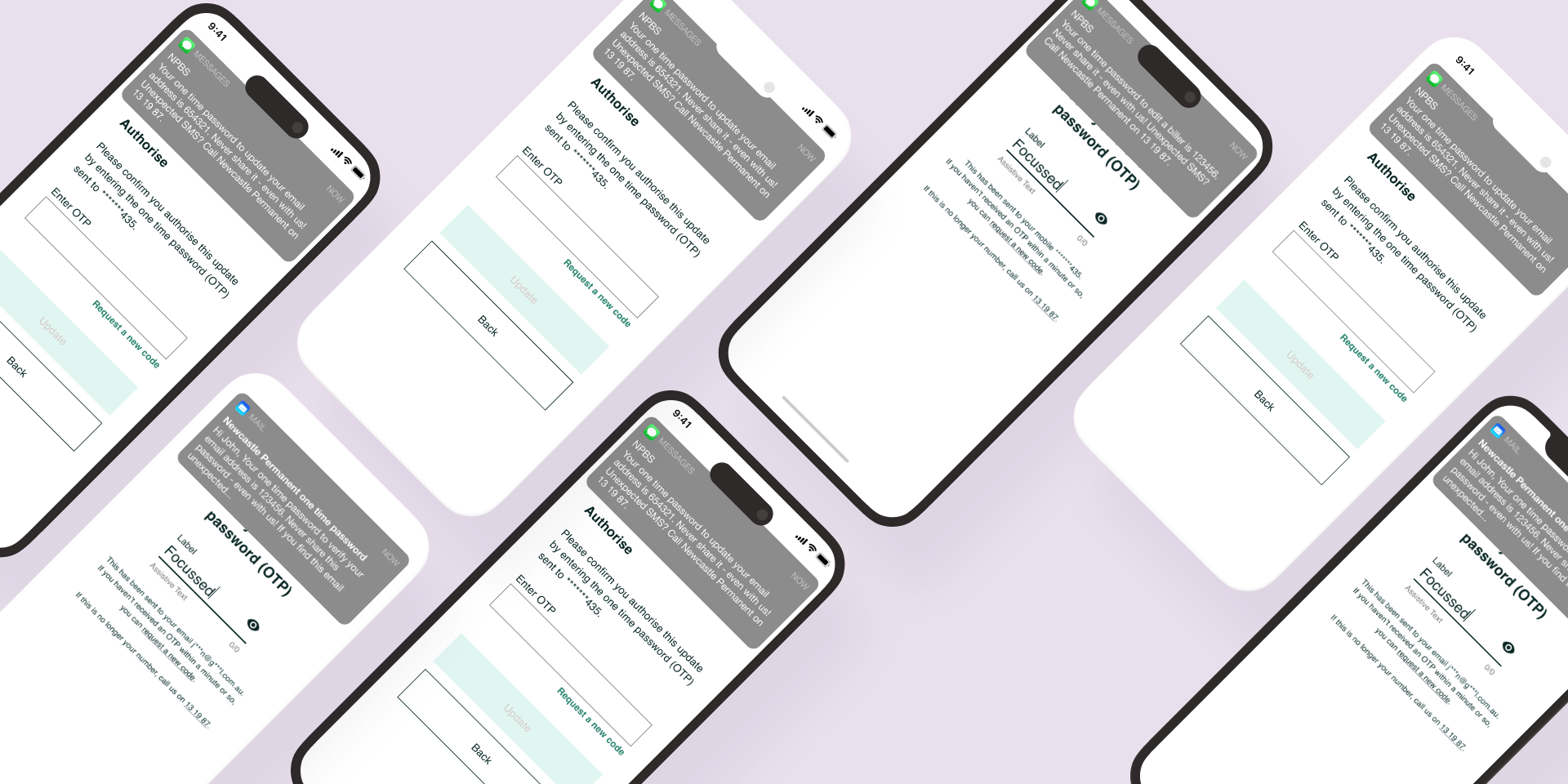
Final OTP content utilised version B showing components as Context Code Warning Action. Messages were was checked for single unbroken message delivery using an SMS Message Length Calculator .
OTP examples with new contextual copy highlighted
Launch material
Launch material consisted of a website and in App promotional hero, as well as an update to existing information on the website Digital banking FAQs
OTP FAQ - Website
iPhone with customer birthday greeting